In today's digital landscape, ensuring network security is of utmost importance for businesses and organizations of all sizes. As the number of connected devices continues to rise, so does the need for effective strategies to protect sensitive information and maintain operational integrity. One such strategy is Meraki Port Isolation, a feature that allows network administrators to control traffic flow and enhance security on their networks. By isolating devices connected to specific ports, organizations can prevent unauthorized communication and mitigate potential threats.
Meraki Port Isolation is particularly vital in environments where multiple users and devices share the same network resources. By implementing this feature, network managers can ensure that devices do not communicate with one another unless explicitly permitted. This not only strengthens security but also enhances overall network performance by reducing unnecessary traffic. As organizations increasingly turn to cloud-based solutions and remote work, understanding Meraki Port Isolation becomes even more crucial in safeguarding digital assets.
This article delves into the various aspects of Meraki Port Isolation, exploring its benefits, configuration, and practical applications. Through a series of questions, we will uncover the significance of this feature and how it can empower network administrators to create safer and more efficient network environments. Join us as we navigate the complexities of Meraki Port Isolation and its vital role in modern networking.
What is Meraki Port Isolation?
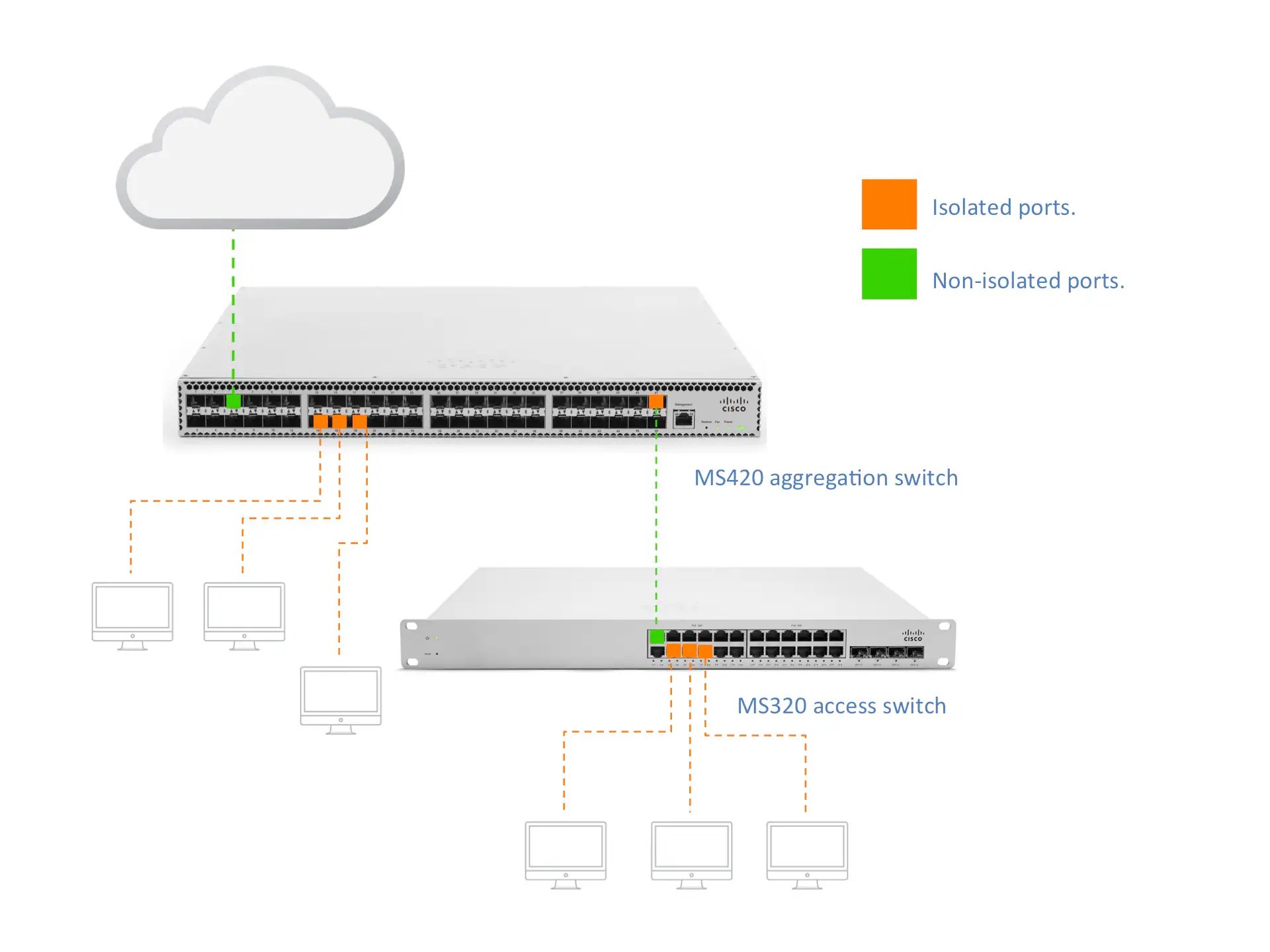
Meraki Port Isolation refers to a security feature found in Cisco Meraki switches, allowing administrators to isolate devices connected to specific ports on the network. This means that devices on isolated ports cannot communicate with each other but can still access shared resources such as the internet. This feature is particularly beneficial in environments where security is a high priority, such as schools, hospitals, and corporate offices.
How Does Meraki Port Isolation Work?
The functionality of Meraki Port Isolation is grounded in the concept of Virtual LANs (VLANs) and Layer 2 isolation. When a port is configured for isolation, it effectively creates a separate broadcast domain, preventing devices on that port from sending or receiving traffic from others on the same switch. This is achieved without the need for complex configurations or extensive networking knowledge, making it accessible for network administrators of all skill levels.
What are the Benefits of Using Meraki Port Isolation?
- Enhanced Security: By isolating devices, unauthorized access and data breaches are significantly reduced.
- Improved Network Performance: Isolated ports help minimize broadcast traffic, resulting in better overall network performance.
- Simplified Management: Meraki’s user-friendly dashboard allows for quick configuration and monitoring of port isolation settings.
- Compliance with Regulations: For organizations subject to data protection regulations, Meraki Port Isolation can help maintain compliance by securing sensitive information.
How to Configure Meraki Port Isolation?
Configuring Meraki Port Isolation is a straightforward process that can be accomplished through the Cisco Meraki dashboard. Here's a step-by-step guide:
What Scenarios Benefit from Meraki Port Isolation?
There are various scenarios where Meraki Port Isolation can be particularly advantageous:
- Public Wi-Fi Networks: In cafes or airports, isolating guest devices prevents them from accessing each other's data.
- Educational Institutions: In schools, isolating student devices helps protect sensitive information and maintain a secure learning environment.
- Healthcare Facilities: Isolating medical devices ensures patient data privacy and compliance with HIPAA regulations.
Can Meraki Port Isolation be Used with VLANs?
Yes, Meraki Port Isolation can be effectively used in conjunction with VLANs. By combining these two features, network administrators can create even more granular security policies tailored to specific user groups or device types. This capability enables organizations to maintain a high level of security while still allowing necessary communications between designated devices.
What Challenges Might Arise with Meraki Port Isolation?
While Meraki Port Isolation offers numerous benefits, there are some challenges that network administrators may encounter:
- Configuration Errors: Incorrectly configuring port isolation can lead to unintended disconnections or communication issues.
- Limited Communication: Over-isolating devices may hinder necessary interactions, such as printer access or file sharing.
- Monitoring and Management: Keeping track of isolated devices may require additional management efforts, especially in larger networks.
Conclusion: Is Meraki Port Isolation Right for Your Network?
In conclusion, Meraki Port Isolation is an invaluable tool for enhancing network security and optimizing performance in various environments. By isolating devices connected to specific ports, organizations can significantly reduce the risk of unauthorized access and data breaches while ensuring that their networks run smoothly. When configured correctly, Meraki Port Isolation can be a powerful security measure that meets the unique needs of businesses and institutions alike.
As you consider implementing Meraki Port Isolation in your network, assess your specific requirements and the potential challenges involved. With the right approach, this feature can play a crucial role in safeguarding your organization's digital assets and ensuring a secure and efficient network environment.
ncG1vNJzZmivp6x7rK3PrKqnZpOkunCv1KWroq6RqbJuvM6soK2hppp6qa3BoqusZ52av6K3yGanqKqkYra0u8uaq6KnnmO1tbnL